Researchers at Imperva have found that the overall number of new vulnerabilities in Content Management Systems in 2018 (17,142) has increased by 21% compared to 2017 (14,082) and by 159% compared to 2016 (6,615). WordPress-related vulnerabilities have exploded and have seen a staggering 300% increase in 2018 compared to the previous year.
More than half of these web application vulnerabilities (54%) have a public exploit available to hackers. In addition, in 38% of the cases, there is no mitigation solution available, such as a patch or a software upgrade”, the report stated.
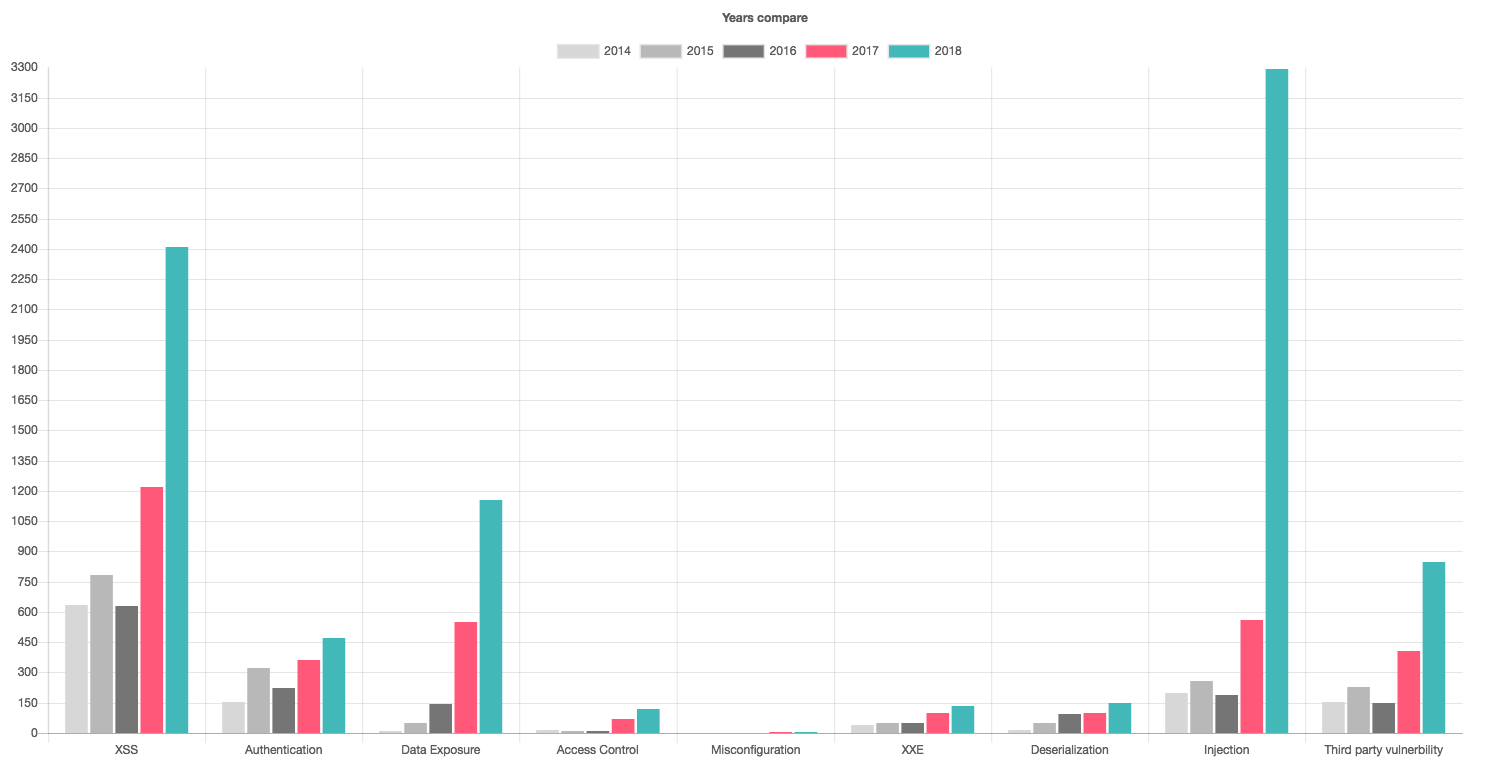
Injection type exploits affecting web apps were the most numerous in 2018, Imperva counting close to 3,300 disclosures. A closer look revealed that almost 1,980 of them allowed remote code execution (RCE) and 1,354 enabled SQL injection attacks. The amount of cross-site scripting (XSS) vulnerabilities doubled since 2017, accounting for 14% of all security flaws reported for web applications last year.
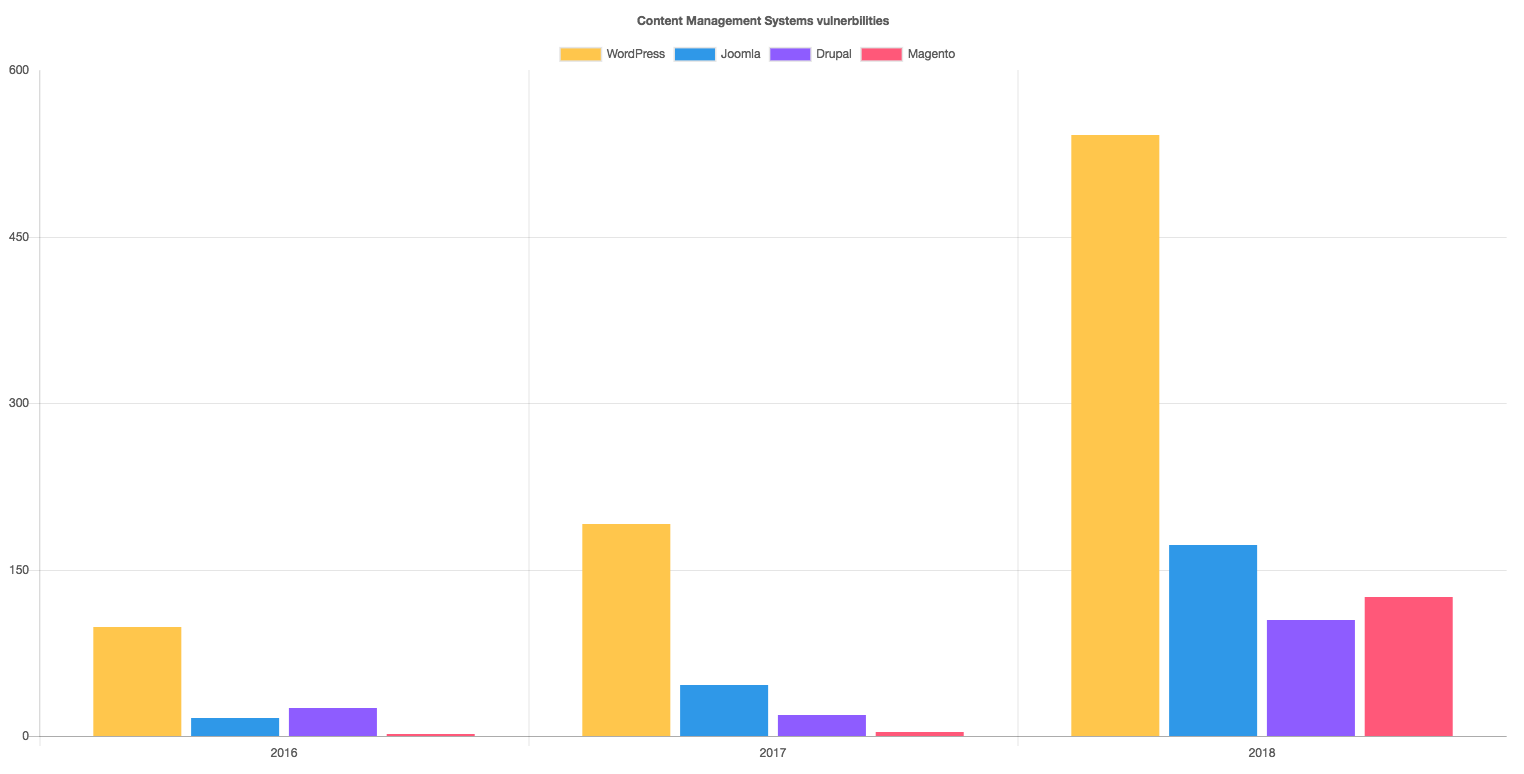
WordPress
WordPress is the most popular content management system (CMS), followed by Joomla and Drupal trailing behind at a safe distance and is used by 59% of all websites using a known CMS. Attackers spent much of their time targeting WordPress, according to the report.
In 2018 the number of vulnerabilities associated with WordPress was 542, while in 2017 less than 200 WordPress-related vulnerabilities were recorded. Joomla and Drupal were affected by less than 150 bugs combined.
Only 2% of the vulnerabilities were found in the WordPress core code. 98% of the detected vulnerabilities are related to WordPress plugins.
Over 55,000 plugins can be found on the official repository of the CMS, many outdated. Only 1914 (3%) of these plugins were added in 2018. The open source nature of WordPress means however that there is no enforcement or any proper process that mandates minimum security standards (e.g. code analysis). Hence, WordPress plugins are prone to vulnerabilities. WordPress patched an array of these vulnerabilities in 2018: Including a critical privilege-escalation vulnerability that could allow an attacker to inject malware, place ads and load custom code on an impacted website; and two bugs rated “medium” in its tooltips plugin.
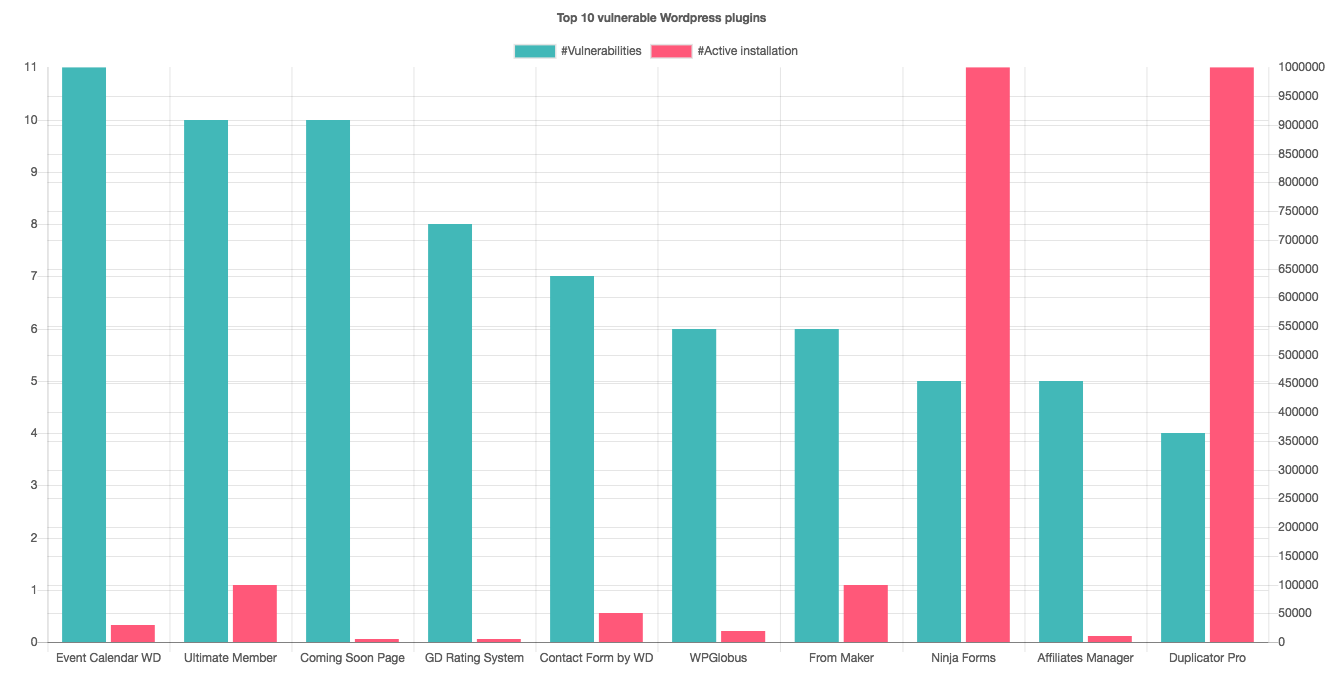
The 10 WordPress plugins that are considered the most vulnerable in 2018 (it should be noted that this does not mean they are necessarily the most-attacked plugins), according to the report:
- Event Calendar WD
- Ultimate Member
- Coming Soon Page
- GD Rating System
- Contact Form by WD
- WPGlobus
- Form Maker
- Ninja Forms
- Affiliates Manager
While WordPress leads the pack in sheer attack numbers, Drupal, the third-most popular CMS had two serious vulnerabilities in 2018, CVE-2018-7600 and CVE-2018-7602. These vulnerabilities allowed an unauthenticated attacker to remotely inject malicious code and run it on default or common Drupal installations and were the root cause for mass attacks that targeted hundreds of thousands of websites in 2018. Most notably last year an infamous highly-critical Drupal bug dubbed Drupalgeddon 2.0 impacted an estimated 1+ million sites running the CMS