A critical remote command execution (RCE) security flaw impacts over half of the Internet’s email servers running Exim, security researchers have revealed today.
CVE-2019-10149 was discovered by Qualys researchers. It is a remote command execution vulnerability that is exploitable instantly by a local attacker and by a remote attacker in certain non-default configurations.
The vulnerability affects Exim, a mail transfer agent (MTA), which is software that runs on email servers to relay E-mail from sender to recipient.
Scale
According to a June 2019 survey of all mail servers visible on the Internet, 57% (507,389) of all email servers use Exim — although different reports would put the number of Exim installations at ten times that number, at 5.4 million.
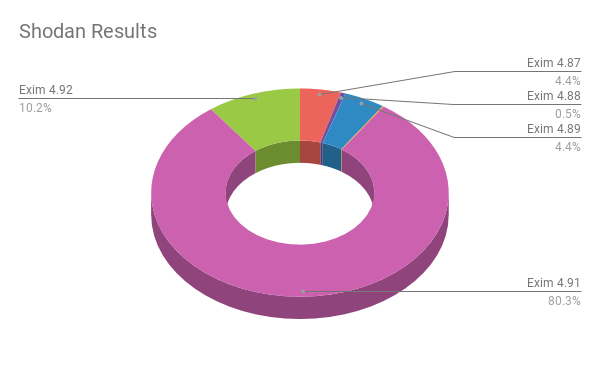
Total Results by Version Number:
- Exim 4.87: 206,024
- Exim 4.88: 24,608
- Exim 4.89: 206,571
- Exim 4.90: 5,480
- Exim 4.91: 3,738,863
- Exim 4.92: 475,591
Analysis
CVE-2019-10149 is a remote command execution vulnerability that was introduced in Exim version 4.87 (released April 6, 2016), when #ifdef EXPERIMENTAL_EVENT became #ifndef DISABLE_EVENT;. Older versions may also be vulnerable if EXPERIMENTAL_EVENT was enabled manually.
In default configurations, a local attacker is capable of exploiting this vulnerability to execute commands as the root user by sending e-mail to a specially crafted mail address on localhost that will be interpreted by the expand_string function within the deliver_message() function. Remote exploitation under the default configuration is possible, but considered to be unreliable, as an attacker would need to maintain connection to a vulnerable server for 7 days.
Qualys researchers have found that in certain non-default configurations, remote exploitation is possible. For instance, if the requirement for verify = recipient ACL was removed from the the default configuration file (src/configure.default), uncommenting out the local_part_suffix = +* : -* under the userforward router in the default configuration, or if Exim was “configured to relay mail to a remote domain, as a secondary MX (Mail eXchange).”
The vulnerability is critical: it allows a local user to easily run commands as root due to an issue in the deliver message code – a local user apparently can just send an e-mail to the address ${run{…}@localhost (where localhost is one of Exim’s local domains) and get the command executed as root
The Exim maintainers have fixed the vulnerability in version 4.92 (released on February 10, 2019) without being aware of it and have now provided patches for the vulnerable earlier versions, although they did point out that those are considered to be outdated and not supported by the developers anymore.
Protection
To confirm you are already running a patched version, you can run this command on the server:
cPanel
rpm -q exim
DirectAdmin
exim --version |head -1
The output will show you the Exim versions that are installed.
cPanel
To ensure that your server has received the patch, please update to one of the following versions:
- 70.0.69
- 76.0.22
- 78.0.27
cPanel & WHM Versions 70 and 76 remain End of Life and will receive no other updates. This is a exception to the policy of cPanel. We still strongly recommend that you keep your servers updated, and continue to run the most recent versions of cPanel & WHM available.
DirectAdmin and Plesk
Exim 4.92 has been included with both control panels since march 2019. Please updat to the latest version available.


